|
Issue
5: April - June 2003
Français
HTML
Espańol
HTML
Previous editions
In this edition:
VISIONS OF THE INFORMATION SOCIETY
1. ICTs
for education and buiding human capital
2. The nature of the information society: A
developing world perspective
3. Network security: Protecting our critical infrastructures
| *“Visions of the
information society” is the title of a series of talks
organized by the ITU Strategy and Policy Unit (SPU) in the
context of the second meeting of the Preparatory Committee
for the World Summit on the Information Society (PrepCom2),
held in February 2003 in Geneva. Material in this issue of
the “Policy and Strategy Trends” pull-out is
based on this series of talks and papers exploring different
aspects of the uses, impact and implications of information
and communication technologies (ICT) in developing and
developed societies. PrepCom2 brought together some 1586
participants from government administrations, private sector
entities, non-governmental organizations (NGO), and civil
society groups representing various sectors of society at
large. |
1. ICTs for education and building human
capital
This article is based on the talk and paper by Frances
Cairncross, Management Editor at The Economist. More
information is available at www.itu.int/visions.
Education is widely recognized as one of the major drivers of
economic development and improvements in human welfare. As global
economic competition grows sharper, education becomes an important
source of competitive advantage, closely linked to economic
growth. It also has a powerful impact on human development.
In developing countries, education is also linked to a whole
batch of indicators of human development. Education of women
influences the health of children and family size. The experience
of Asian economies, in particular in the past two decades, has
demonstrated the benefits that public investment in education can
bring. Another benefit of a high standard of education delivered
at the national level is that young people with strong academic
potential are more likely to stay in their home countries. This
can help to stem the “brain drain” from poorer nations to
richer ones. In richer countries, education is seen as important
not just in the early years, but also in later life as a way to
improve and update skills and capabilities of the workforce as it
grows older and the pace of technological change quickens.
Many constraints stand in the way of delivering education to
the right people at the right time. In developing countries, there
is frequently a shortage of qualified school teachers,
particularly for people who live in scattered communities in rural
areas. Money for books and teaching materials are often scarce. In
wealthier countries, money is also a problem: in particular, the
cost of university education has risen sharply, and students are
increasingly expected to directly meet all or part of the cost.
There is also the problem of time in higher institutions of
learning and training: students who are already in full-time
employment find it hard to take part in a university course
offered at conventional times of day. Finally, employers, keen to
train staff, are often acutely conscious of the costs of taking
people away from their main job in order to attend training
courses. They are therefore eager for more efficient and flexible
ways to deliver information to employees.
All these factors have encouraged an interest in the use of
ICTs to deliver education and training. Experience so far has been
broadest in developed countries. Easily the largest investments in
ICT have been in the United States. Among developing countries,
China stands out particularly for the efforts it is making to use
ICT to expand education.
Evaluating the effectiveness of ICTs in the classroom is just
as hard as evaluating other interventions in education. What is
clear is that ICTs are potentially a useful tool both for managing
educational institutions and for gaining access to teaching
materials. For developing countries, teaching computer skills to
youngsters may benefit inward investment. But on the other hand,
as educational policy-makers for schools — notably those in
developed countries — have become more insistent on measuring
benefits of ICTs in terms of academic results, there is a lack of
evidence that using ICTs actually boosts schoolchildren’s
performance. One recent study found no evidence that the use of
ICT produced better educational results.
Conversely, ICTs in education seem to hold much promise in
expanding access to education to those who would otherwise miss
out on the opportunity to learn and train. In universities in
particular, there is evidence that ICTs have a valuable
contribution to make. Well-designed ICTs can allow educators to
reach new groups of potential students, particularly mature
students, lifelong learners, students with physical disabilities,
students in employment and students who are far from education
centres. It is notable though, that endeavours by universities in
developed countries to boost their incomes through distance
teaching have largely failed to generate much profit, so the
benefits are perhaps better measured in terms of increasing access
to education, as well as a number of spin-offs such as the
development of increasingly sophisticated ICT learning materials.
In developing countries, electronically delivered courses may
make the difference between some education and none at all for
people in remote rural areas. For aid donors, it is thus
especially worthwhile to invest in opportunities for remote
learning. ICTs are most likely to be cost-effective when used to
reach very large numbers of students (a common challenge in
developing countries); when used for research; and when used by
administrators. It would be a mistake to think though, that making
computers available is adequate as a one-time investment.
Maintaining ICT-based learning projects involves both heavy
initial costs to prepare teaching materials, and recurrent costs
to replace hardware and software.
Not surprisingly, developing countries tend to have far fewer
computers per student than richer countries. In the United States,
the ratio of students to computers dropped from 125 to 1 in 1983
to 5 to 1 in 2000. One assessment of computers in classrooms in
developing countries found that Costa Rica had an average of
between 53 and 73 students per computer in its schools, while
Chile had 68 to 137 students per machine.
Those who live on 1 USD a day cannot afford to pay 1
USD per minute to use the Internet
While the benefits of access to knowledge and
information are proven, and it is recognized that
education is an important driver of economic growth, the
fundamental hurdles to be overcome in underprivileged
societies are still infrastructure, cost, and access to
computers and to relevant content. For these to be
overcome, much needs to be done to help countries make
access possible, through availability of computers,
training of teachers, and the provision of low-cost
Internet access.
|
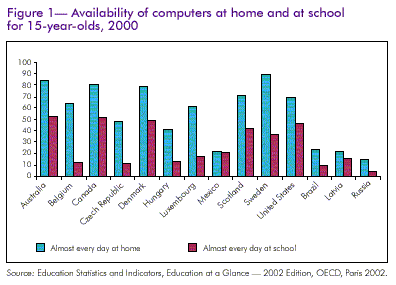
One of the most important differences between countries is the
availability of hardware. In the developed world, youngsters tend
to have better access at home than at school. In Sweden, for
example, a survey of 15 year-olds in 2000 found that 90 per cent
had almost daily access to computers at home, but only 37 per cent
at school. In Latvia, by contrast, only 15 per cent of 15
year-olds had near-daily access at home, and a mere 5 per cent at
school. At university level, computer ownership is almost
universal in richer countries. In developing countries, it is far
lower (see Figure 1). This inevitably affects the ways ICT can be
applied.
Getting the best from ICTs depends on several variables,
including the appropriate design of software and hardware; the
training and attitude of instructors; and the realization that
different students have different requirements. It also requires a
willingness to experiment: effective use of ICTs in education and
training is likely to require quite different pedagogical
techniques from traditional classroom teaching. These will
probably take a long time to devise and disseminate.
Perhaps the most important lesson to take into account is that
what works in a country with high levels of computer access and
low telephone costs will not necessarily transfer to somewhere
with few computers and expensive connection charges. The potential
for using ICTs well in education and in building human capital
depends on a number of factors that differ from one country to
another, and especially between developed and developing
countries. It is important for countries to bear these differences
in mind when making investments.

2. The nature of the information society: A
developing world perspective
| This article is based on a
presentation and paper prepared by Mr Madanmohan Rao, ICT Consultant
and Author (India). Mr Rao’s paper charts the industry and instrument
aspects of ICTs in developing nations, using a comparative framework he
has developed over the years, called the “8 Cs” of the digital
economy: connectivity, content, community, commerce, culture, capacity,
cooperation and capital. This framework is described briefly in the
article above. More information is available at www.itu.int/visions. |
There are two ways of looking at ICTs: as an instrument,
and as an industry. As an instrument, affordable and usable ICTs can indeed
transform the way societies work, entertain, study, govern and live — at
the individual, organizational, sector, vocational and national levels. As
an industry, ICTs represent a major growing economic sector covering
hardware, software, telecommunications/datacom and consulting services.
Through both lenses — industry and instrument — the
performance of developing nations lags behind that of developed nations, but
interesting patterns of variation and pockets of excellence are emerging.
For instance, countries like India and the Philippines have ICT industries
that are exporting software and attracting outsourcing contracts, but they
also have looming digital divides where ICTs are not neither accessible nor
affordable as instruments for a majority of the population.
Table 1 — The “8 Cs” of the information society
|
| |
ICTs as an instrument |
ICTs as an industry |
| Connectivity |
How
affordable and widespread are ICTs (e.g. PCs, Internet access, software)
for the common citizen? |
Does the
country have ICT manufacturing industries for hardware, software,
datacom solutions and services? |
| Content |
Is there useful
content (foreign and local) for citizens to use in their daily lives? |
Is content being generated in
local languages and localised interfaces? Is this being accessed/used
abroad? |
| Community |
Are
there online/offline forums where citizens can discuss ICT and other
issues of concern? |
Is the country
a hub of discussion and forums for the worldwide ICT industry? |
| Commerce |
Is there
infrastructure (technical, legal) for e-commerce for citizens,
businesses and government? How much commerce is transacted
electronically? |
Does the country have indigenous
ecommerce technology and services? Are these being exported? |
| Capacity |
Do
citizens and organizations have the human resources capacity (technical,
managerial, policy and legal) to effectively harness ICTs for daily use? |
Does the
country have the human resources capacity (technical, managerial,
policy, legal) to create and export ICTs? |
| Culture |
Is there a
forward-looking, open, progressive culture at the level of
policy-makers, businesses, educators, citizens and the media in opening
up access to ICTs and harnessing them? Or is there nervousness and
phobia about the cultural and political impacts of ICTs? |
Are there technical experts,
entrepreneurs and managers pro-active and savvy enough to create local
companies and take them global? |
| Cooperation |
Is
there adequate cooperation between citizens, businesses, academics, NGOs
and policy-makers to create a favourable climate for using ICTs? |
Is there a
favourable regulatory environment in the country for creating ICT
companies, and links with the diaspora population? |
| Capital |
Are there enough
financial resources to invest in ICT infrastructure and education? |
Is there a domestic
venture capital industry; is it investing abroad as well? How many
international players are active in the local private equity market? Are
there stock markets for public listing? |
While analysing the impact and potential of ICTs by economic
sector is a useful first step to overcoming the divide between developing
and developed nations, it misses a crucial factor: ICTs like the Internet
cannot be interpreted merely as digital forms of telecommunications, or as
mere computers, or as media outlets. Many early well-intentioned ICT
projects in developing countries have not meet with the success they might
have because they were too technology-centric or stopped merely at the
installation phase of computers. The information society is not just about
connectivity to the global information infrastructure, but about the content
that is accessible, the communities that congregate online and offline, the
embedded and emerging cultural attitudes, the commercial and other motives
behind such activities, an attitude of cooperation and lifelong learning,
and a capacity for creating and governing such information spaces. The
information society is not just about passively using “black box”
technologies, but about actively creating and shaping the underlying
technical, information and service infrastructure. Thus, a more powerful
framework is needed which can contextualize ICT diffusion, usage and
creation with respect to these attributes.
Coupled with these two aspects of ICTs (usage and creation),
the “8 Cs” approach (see Table 1) can help to tease apart some of the
key challenges in implementing the vision of knowledge societies, such as
increasing ICT diffusion and adoption, scaling up ICT pilot projects,
ensuring sustainability and viability of ICT initiatives, creating ICT
industries, and systematically analysing research on the global information
society. The role of local stakeholders, multilateral agencies, donor
institutions and the development community is highlighted.

3. Network
Security: Protecting our critical infrastructures
| This
article is based on a paper
prepared by Seymour Goodman, Professor College of Computing
& The Sam Nunn School of International Affairs, Georgia
Institute of Technology. The other two authors, Ms. Pam Hassebroek
and Mr. Hans Klein, also work at the Georgia Institute of Technology.
More information is available at www.itu.int/visions.
|
Cyberspace—the Internet and
other computer-based networks—is becoming one of the most important
infrastructures that characterize modern societies. Among the networks of
cyberspace are systems that control and manage other infrastructures such as
banking, emergency services, energy delivery, and many transportation and
military systems. Thus, many regions’ economic and social stability may
depend on these networks. The computer-communications networks of cyberspace
are the underlying technological bases that will enable all “visions of
the information society.”
Dependencies
on networks for communication and business operations continue to grow along
with the growth of cyberspace. Today, the Internet in particular, which has
grown without any planning or central organization, is a vast network of
networks. As of 1989, the Internet interconnected around 20 countries and
100,000 hosts. The majority of those hosts were located in the United
States. As of early 2002, there were hundreds of millions of host computers
and perhaps at least a half billion users worldwide.
More than half of the users are now located outside the U.S. and perhaps a
quarter outside of the OECD countries. It is increasingly beyond the scope
of single nations to control users who would inflict damage to or via the
systems of cyberspace.
Destructive
acts using computer networks have cost billions of dollars and increasingly
threaten the resources of network-connected critical infrastructures.
Threats
to network infrastructures are potentially extensive not only as their value
increases in terms of the infrastructures themselves, the value of hosted
services, and the value of what is located on them, but also because of
their widespread and low-cost access. These infrastructures of cyberspace
are vulnerable due to three kinds of failure: complexity, accident, and
hostile intent. However, we lack a comprehensive understanding of these
vulnerabilities—largely because of the extraordinary complexities of many
of the problems, and perhaps from too little effort to acquire this
understanding. But there is ample evidence that vulnerabilities are there:
examples of all three kinds of failure abound, and vulnerabilities are found
almost every time people seriously look for them.
Within
this vast, complex cyberspace system, it is so simple to connect that users
of today’s systems require few skills and little understanding of the
underpinnings. Thus, we require not only technical protections but also an
awareness and alertness on the part of all users to the dangers inherent in
the use of any system connected to a network. Attacks so far have been
limited. However, many believe that it is only a matter of time before
prolonged, multifaceted, coordinated attacks are going to find those network
vulnerabilities and exploit them to produce serious consequences. Prudence
dictates better protection against accidents and attacks before things get
much worse. All realizations of “visions of the information society” are
going to be severely limited if the people in that society do not trust or
feel secure with the underlying infrastructures.
Alertness
to the dangers requires protections that can stay abreast of changing attack
modes. An essential part of a defence strategy is continual network
monitoring and innovation in monitoring techniques to minimize the potential
for damage from the actions of cybercriminals. However, there are multiple
stages of defence and a cycle of understanding, which is a complex system in
itself. The overlapping stages of prevention and/or thwarting an attack,
incident management, reconstituting after an attack, and improving defender
performance by analysis and redesign are essential to understanding the
elements of each network intrusion attempt. Invariably, gaining this
understanding involves some ability to trace the route of attack to the
source so that the attacker can be identified. International cooperation can
help to bring about success in this effort, in situations where it would be
impossible otherwise.
Faced
with the possibility of disruption of critical infrastructures in ways that
could have serious consequences, governments should be expected to implement
prudent defence plans. Each country should first identify those
infrastructures and their interdependencies that are critical to its
survival and to its social and economic well-being. Planning for specific
defences of these identified infrastructures may usefully include both
passive
and active defence forms.
Since an
infrastructure system is typically a mix of public and private ownership,
the various owners are likely to have different motivations for and roles in
such planning for its protection. Private owners will seek solutions that
maintain revenues and the confidence of their markets. Governments will
pursue policies that focus on longer-term aspects of protection, seeking to
protect their economies and national security, to maintain law and order,
and to reduce cumulative losses.
The
combination of diversity in its users and its international dimension
contributes much to the promise of cyberspace networks and, at the same
time, creates the most difficult problems. Its international character is
central to the “vision” for many of the network’s visionaries. And
this characteristic creates a requirement of international cooperation for
increasing the security of the network’s infrastructures. Defence policies
and practices must apply globally to be effective. The ways in which
cooperation can help to increase security are numerous, but in this paper,
we focus on some of the most clear and expedient avenues to curtailment of
criminal activity. These activities include: standardization, information
sharing, halting attacks in progress, legal coordination, and providing aid
to developing nations.
In many
aspects of network connection, the issue of standards offers both an
opportunity for improvement in security and an opportunity for clearer
avenues to abuse. Standard protocols, applications, workstation and server
configurations all play a role in providing either a system of trust or a
platform for criminals. Security as a clear and present priority for network
operation needs to be a prime focus for future development standards and
remedial activity.
Information
sharing is required in order to develop security standards for successful
product development and effective standard security practices. International
collaboration in all aspects of network operations can help to ensure the
best possible protection for the valuable assets of its users. A cyberattack
in progress can be minimized by the widespread communication of such an
event to users and system operators. Information sharing is also essential
in order to locate and prosecute cyber criminals.
One form
of international cooperation that has been much discussed is the potential
for harmonization of laws among countries that can help to prevent
cybercrime and provide a deterrent to cybercriminals. Criminals may
currently circumvent jurisdictions and places with strong technical and
legal barriers in order to find the cracks in the system where it is safe to
create problems. We need to close these cracks.
All of
these forms of cooperation work better, when all nations are equally capable
of carrying their share of responsibilities. At present, this is not the
case. There are many countries where people with high-level technical skills
are not present in adequate numbers. A cooperative effort among nations can
assist with these needs for training and equipment.
Achieving
global coordination in these areas is not an easy task. It requires legal
and administrative policies in order to create a framework for global
interaction. Policies include setting well-defined boundaries for legal
actions, the creation of an international organization, and possibly a
multilateral treaty. Cybercrime and the potential for cyberterrorism not
only creates a requirement for intergovernmental machinery, but, given our
growing dependencies on the networks, adds a sense of urgency to the task.
Given the
urgency of the problem as well as the difficulty of constructing global
frameworks, it is appealing to look for shortcuts. One attractive
alternative would employ private coordination, perhaps based on the model of
the Internet Engineering Task Force (IETF). However, private groups cannot
contribute directly in active defence or in legal harmonization. In
addition, privatization allows a policy process that may lack proper
international representation and democratic participation. Such deficiencies
in an international organization could create barriers to effectiveness in
the process of addressing network security.
We
believe that a necessary way to proceed is through international,
intergovernmental coordination. The types of cooperation described above
suggest a highly interactive partnership in pursuit of common goals. We
present in this paper what we conceive as the ideal model for such a
construction. We see four required features in this model: First, all
cooperating countries would share a common baseline perception of what
constitutes criminal behavior in cyberspace. Second, each of the governments
of the world would have substantial competence to deal with the problem of
preventing, thwarting, etc. and punishing attacks on cyber systems. This
includes capabilities and policies in passive defence to provide effective
security within each government’s jurisdiction. Third, each would have
substantial capability in active defence, and a competent national authority
for engaging in active defence. Finally, international responses to
transnational attacks would be covered under a near-universal umbrella
convention that would permit timely action under established procedures.
While initiatives exist in international cooperation to increase security,
the present reality is still far from this ideal model.

| For further information on Policy
and Strategy Trends, please contact: ITU Strategy and Policy Unit,
International Telecommunication Union, Place des Nations, CH-1211 Geneva 20
(Switzerland). Fax: +41 22 730 6453. E-mail: spumail@itu.int
. Website: www.itu.int/spu/ |
|